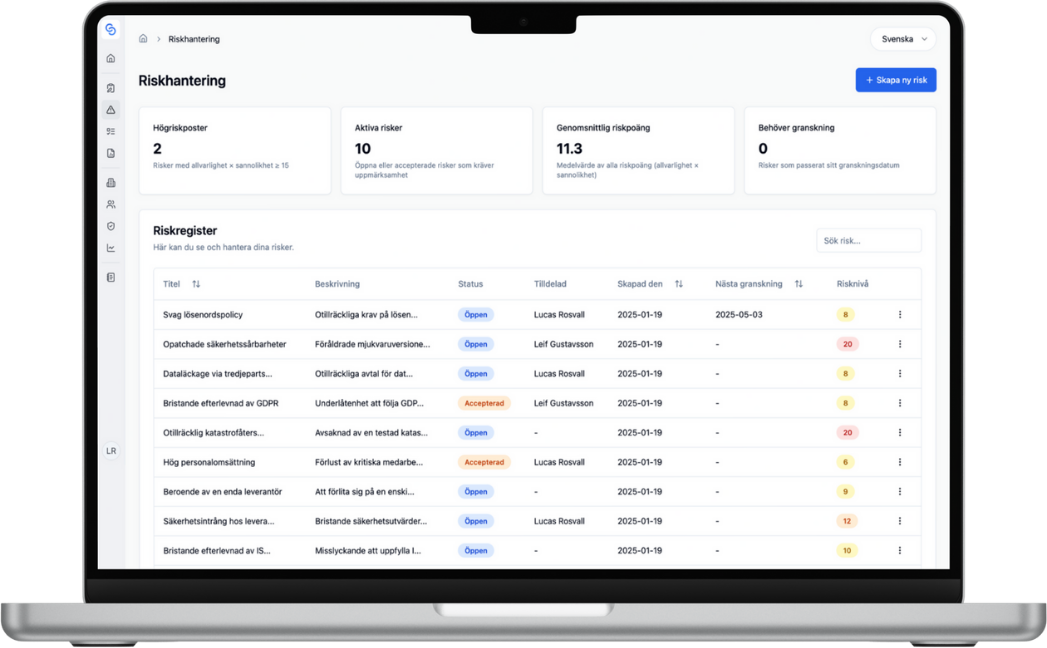
Visualize the entire chain
In ChainSec, you see exactly how everything is connected. Click on an asset to see which risks threaten it. Click on a risk to see which controls mitigate it. This gives you full traceability and makes it easy to report to management and the board.
See demo of the flow